# V2V와 V2I 의 이해
# V2V 통신 기술이란?
: V2V는 Vehicle to Vehicle의 약자로, 이동 중이거나 정차 중인 차량들 간의 신호 또는 데이터를 송수신하는 무선 통신 기술로, 일정 범위 내에 있는 자동차들이 무선 통신을 통해 각자의 위치/속도 정보와 주변 교통상황 정보 등을 주고받으며 갑작스러운 교통사고를 예방할 수 있는 시스템이다.

- 동일한 서비스에서의 V2V 사용 여부와 양상
| V2V 기능 포함 | V2V 기능 미포함 | |
| 자율주행차 | V2V 통신을 통해 다른 차량과 소통 | V2V 통신 없이 자율적으로 운행 |
| 교통정보 서비스 | V2V 통신을 통해 다른 차량으로부터 교통정보 수집 | 인프라 기반 교통정보 수집 및 제공 |
| 차량충돌 회피시스템 | V2V 통신을 통해 다른 차량과의 거리, 속도 등 정보 공유 | 차량 자체 센서 및 카메라를 활용한 충돌 회피 시스템 |
| 차량진단 서비스 | V2V 통신을 통해 다른 차량으로부터 진단 정보 수집 | 인터넷을 통한 원격 진단 및 자가진단 기능 제공 |
| 주차관리 시스템 | V2V 통신을 통해 주변 차량들과 주차장 상황 공유 | 인프라 기반 주차장 정보 수집 및 주차 관리 시스템 |
+ 참고 자료
http://www.fescaro.com/ko/archives/467/
기술블로그 - INSIGHT - 페스카로(FESCARO) - 자동차 소프트웨어 전문기업(자동차 사이버보안, 제어기,
페스카로는 자율주행차, 전기차, 커넥티드카 등 미래차의 모든 SW솔루션을 제공합니다. 자동차 사이버보안부터 게이트웨이 제어기, V2X, SDV까지 다가오는 미래차 산업의 혁신을 주도합니다.
www.fescaro.com
V2X 기술 소개 - 카네비모빌리티
carnavi.com
# V2V 오작동과 그 위험성
: V2V 오작동은 다양한 요인에 의해 발생할 수 있으며, 그 대표적인 예시는 아래와 같다.
① 기술적인 결함 및 버그같은 SW적 문제로 인한 오작동
② 외부의 약의적 공격으로 인한 오작동
③ V2V 센서 오류 등 하드웨어적인 문제로 인한 오작동
+ 참고 자료
DBpia
논문, 학술저널 검색 플랫폼 서비스
www.dbpia.co.kr
V2I 오작동에 의한 자율주행자동차의 위험성 분석
최근 자율주행자동차의 개발이 활발하게 진행되면서 더욱 안전하고 쾌적한 주행을 위해V2V, V2I 등 V2X 서비스를 활용하는 자율주행시스템의 중요성이 높아지고 있다. 환경 센서에기반한 부분 자
www.kci.go.kr
# V2I란?
: V2I는 Vehicle to Infrastructure의 약자로, 차량 내에 설치된 통신 단말기와 정보를 서로 교환할 수 있는 일종의 기지국을 도로 곳곳에 설치하여 차량으로부터 주행 정보를 수집하고, 이를 중앙 서버에서 분석하여 교통상황 및 사고정보 등을 차량에게 제공하는 기술입니다.

- V2I 기술이 필요한 이유
: 교통 흐름 최적화
--> V2I 기술 사용시 교콩 인프라와 차량 간 정보 교환을 통해 교통 상황을 실시간으로 파악 가능. 이를 통해 교통 신호의 실시간 제어 및 차량 운행 경로 조정, 속도 조절 등으로 교통 흐름을 최적화할 수 있음
: 교통 안전 향상
--> 교통 인프라에서 제공하는 교통 관련 정보를 차량에 제공함으로써 차량 운전자에게 실시간으로 교통 상황 전달 가능. 추가적으로 인프라에서 차량으로 위험 상황에 대한 정보를 전달함으로써 차량 운전자가 적절한 조치를 취할 수 있도록 조력하여, 교통사고 예방에 기여함
: 운전 편의성 개선
--> 차량 운전자는 V2I 기술을 통해 인프라에서 제공하는 정보를 토대로 차량의 운행 경로, 주차장의 위치 등을 쉽게 파악할 수 있음
+ 참고 자료
V2I(Vehicle-to-Infrastructure) 통신이란 무엇이며 왜 필요할까요?
V2I 기술이 안전에 도움을 주고 이동성을 향상시키며, 미래의 도로를 가능하게 하는 방법을 확인해보세요.
www.3m.co.kr
https://www.aitimes.kr/news/articleView.html?idxno=20204
[기고] 자율주행 기술: (4) 자율주행차를 가능하게 하는 'V2V/V2I' 통신 - 인공지능신문
필자, 마크 패트릭(Mark Patrick)은 세계에서 가장 다양한 글로벌 반도체 및 전자부품들을 보유 및 유통기업인 마우저 일렉트로닉스(Mouser Electronics)의 유럽·중동·아프리카(EMEA. Europe, Middle East, and...
www.aitimes.kr
https://smartits.tistory.com/292
V2X (V2V, V2I, V2P) 개요
V2X(Vehicle-to-Everything)는 V2V(Vehicle-to-Vehicle), V2I(Vehicle-to-Infrastructure), V2P(Vehicle-to-Pedestrian) 통신으로 구성된 지능형 교통 시스템을 말합니다. V2X는 광범위한 전송 및 트래픽 관련 센서 간의 고대역폭,
smartits.tistory.com
# V2I와 보안 위협_TCP SYN Flooding attack
: TCP SYN Flooding 공격은 대상 서버에 대한 TCP 연결을 생성하는 과정에서 SYN 패킷을 보내고, 서버로부터 SYN+ACK 패킷을 받은 후에 ACK 패킷을 보내는 3-way handshake 과정을 악용하는 공격이다.
| 3-way handshake 과정 | 클라이언트측 | 서버 측 |
| SYN | SYN 패킷 전송 | - |
| SYN + ACK | - | SYN + ACK 패킷 전송 |
| ACK | ACK 패킷 전송 | - |
TCP SYN Flooding 공격을 수행하는 공격자는 대량의 SYN 패킷을 대상 서버로 보내어 대상 서버가 SYN+ACK 패킷을 전송하도록 유도한다. 그리고, SYN+ACK 패킷을 수신한 공격자는 ACK 패킷을 보내지 않고, 대상 서버의 half-open 상태로 남겨두는데, 이를 반복적으로 수행하면 대상 서버는 half-open 상태로 연결 정보를 가득 채우게 되어 새로운 연결 요청을 처리하지 못하게 된다. 따라서, 대상 서버는 서비스 거부 상태가 되어 정상적인 서비스를 제공하지 못하는 상태에 빠지게 된다.

+ 참고 자료
https://www.imperva.com/learn/ddos/syn-flood/
What is a TCP SYN Flood | DDoS Attack Glossary | Imperva
In a SYN flood attack, the attacker sends repeated SYN packets to every port on the targeted server, often using a fake IP address. The server, unaware of the attack, receives multiple, apparently legitimate requests to establish communication.
www.imperva.com
# V2I와 보안 위협_Duplicate Address Detection(DAD) DoS
: Duplicate Address Detection (DAD)은 IPv6 네트워크에서 주소 충돌을 방지하기 위한 메커니즘으로, 이를 통해 잘못된 IPv6 주소 할당을 방지하고, 네트워크 상에서 고유한 주소를 보장할 수 있습니다.
이러한 DAD 기술을 악용한 공격이 바로 Duplicate Address Detection(DAD) DoS 공격이다. 이 공격을 대개 유사한 주소를 대량으로 생성하여 네트워크의 성능을 저하시키고 시스템의 가용성을 저하시키는 것을 목적으로 한다. 이러한 DAD DoS 공격은 네트워크의 대역폭을 차지함과 동시에 주소 충돌 검사를 막아 타 장치들이 IPv6 주소를 할당받을 수 없게 만든다.

+ 참고 자료
https://journals.plos.org/plosone/article?id=10.1371/journal.pone.0214518
DAD-match; Security technique to prevent denial of service attack on duplicate address detection process in IPv6 link-local netw
An efficiently unlimited address space is provided by Internet Protocol version 6 (IPv6). It aims to accommodate thousands of hundreds of unique devices on a similar link. This can be achieved through the Duplicate Address Detection (DAD) process. It is co
journals.plos.org
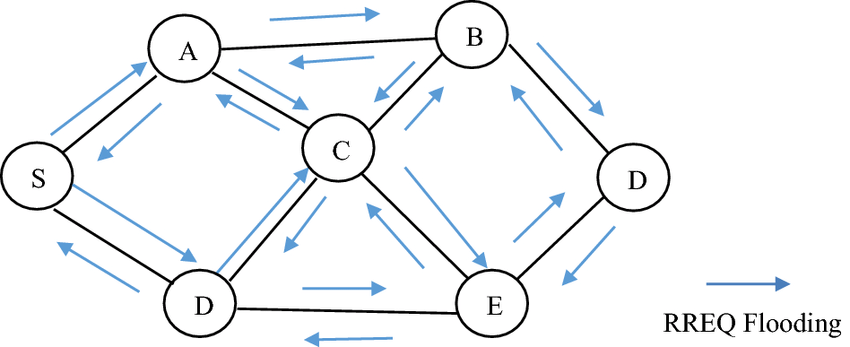
# V2I와 보안 위협_RREQ Flooding attack
: RREQ Flooding Attack은 Ad Hoc 무선 네트워크에서 발생하는 공격 중 하나로, 네트워크에 대한 라우팅 정보를 요청하는 RREQ 메시지를 대량으로 전송하여 네트워크 대역폭을 차지하거나, 네트워크를 불안정하게 만드는 공격이다.
--> 일반적으로 AODV 라우팅 프로토콜에서 경로 탐색은 on-demand 방식으로 수행되는데, 이 RREQ Flooding Attack은 on-demand 방식에서 진행되는 RREQ 패킷 전송을 악용한 공격이라고 볼 수 있다.
- RREQ란?
: Ad Hoc 무선 네트워크에서 경로 탐색을 위해 전송되는 Route 리퀘스트 메시지
- AODV(Ad-hoc On-demand Distance Vector)
: Ad Hoc 무선 네트워크에서 사용되는 라우팅 프로토콜 중 하나로, on-demand 방식으로 라우팅 정보를 검색
--> 라우팅 테이블 유지를 위해 다음 홉 노드에게 라우팅 정보 요청을 전송하고, 이를 통해 목적지까지의 경로를 구성
- On-Demand 방식
: 라우팅 정보가 필요한 경우에 한해서만 라우팅 정보를 탐색하는 방식으로, 라우팅 테이블의 업데이트 빈도를 낮출 수 있어 라우팅 정보 유지 시 자원의 효율적 사용이 가능하다는 장점이 있다.
+ 참고 자료
https://ieeexplore.ieee.org/document/7755330
Simulating and analyzing RREQ flooding attack in Wireless Sensor Networks
Broadcast nature of Wireless Sensor Networks subjects them to assortment of various attacks. Denial of service is the most common class of attack launched against wireless sensor networks. To mitigate these attacks it gets imperative to comprehend their ci
ieeexplore.ieee.org
# V2I와 보안 위협_BSM DoS
: BSM DoS는 BSM 메시지를 대량으로 생성하여 네트워크의 대역폭에 악영향을 주는 공격이다. 위 공격은 자율 주행 차량 간 통신을 방해하여 심각한 교통사고를 유발할 위험성이 있다.
- BSM 이란?
: BSM은 Basic Safty Message의 약자이자 자율 주행 차량에서 다른 차량과의 통신에 사용되는 메시지로, 주로 차량 간 안전 정보 교환에 자주 사용됨
- BSM DoS 공격의 예방법
① BSM 메시지 필터링 기능을 젹용
② 차량 간 통신 대역폭을 제한
③ BSM 메세지 생성자의 신원 확인
④ 비정상적인 트래픽 차단
+ 참고 자료
https://www.ibm.com/docs/en/zos/2.2.0?topic=discovery-duplicate-address-detection
Duplicate address detection
Duplicate address detection (DAD) is used to verify that an IPv6 home address is unique on the LAN before the address is assigned to a physical interface (for example, QDIO). z/OS® Communications Server responds to other nodes that are doing DAD for IP ad
www.ibm.com
https://koreascience.kr/article/JAKO202013965595414.kr
자율주행자동차 V2V 통신환경에서의 DoS 공격 및 대응기술 동향 연구 -Review of KIISC
Ⅰ. 서론 최근 국내뿐만 아니라 전 세계적으로 자율주행자동차에 대한 관심이 매우 증가하고 있다. 자율주행자동차가 큰 이슈가 되면서 자율주행과 관련된 기술을 개발하는 곳은 단순 자동차제
koreascience.kr
'✒️ INTERLUDE > 2023 Autonomous Driving & Network Study' 카테고리의 다른 글
| [3주차] LIN Bus & V2X 의 이해 (0) | 2023.04.06 |
|---|---|
| [2주차] CAN 통신의 이해: CAN Protocol 및 통신 시스템 & CAN Dos Attack (0) | 2023.04.05 |
| [1주차] 자율주행 자동차 & 커넥티드 카 동향 (1) | 2023.03.29 |


